In this guide I will explain how to set up wake on lan over the internet without introducing security vulnerabilities. This will be done by allowing only one peer with a static ip to access the device from the internet.
Firewall
First check your PC supports wake on LAN. On some mainboards you have to enable it in the bios in addition to the device manager. Additionally sometimes energy saving options have to be disabled. Enable only listen for „magic packet“ and not „any packet“ or „pattern match“, to prevent accidental wake ups.
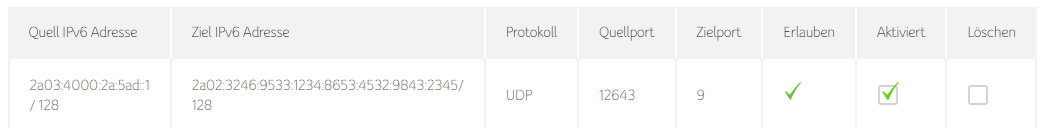
Look up the IPv6 address of your PC (not the temporary addresses) and add an exception to the firewall of your router. This example is for a connectbox by unitymedia:
Use the peer with a static IPv6 address as the source (in my case a server) and your pc as the target. Only allow UDP with a random source port. As a target port I used 9, because it seems to be a common port for wake on lan and it’s important that nothing on the pc is listening to this port. Also add a firewall rule on the pc that blocks this port.
Wakeup script
Wake on Lan with magic packet works by sending any type of IP packet containing the „magic“ sequence generated from the MAC address of the target device. This can be sent using any tool capable of sending single packets. I chose socat, because it easily allows specifying a source port and is available on any linux device. There are other tools available for other systems. The script is based on this Stackoverflow answer which explains how to do the same using netcat.
The script uses the MAC of the target device to generate the magic packet and sends it using socat. Edit it to contain your PC Mac, PC Ip and Source port you allowed in the firewall.
#!/bin/bash
MAC=AB:CO:FF:EE:AB:CD
IP=2a02:3246:9533:1234:8653:4532:9843:2345
PORT=9
SOURCE_PORT=12643
echo -e $(echo $(printf 'f%.0s' {1..12}; printf "$(echo $MAC | sed 's/://g')%.0s" {1..16}) | sed -e 's/../\\x&/g') | socat - udp6-datagram:[$IP]:$PORT,sp=$SOURCE_PORT
With my provider (unitymedia) I seem to keep the same public IPv6 prefix forever, so the address of the pc does not change. If it changes with your provider you might have to either occasionally change the ip or add a task on the pc which automatically saves the current ip to the server.
Security
This solution should be very secure, because only one port is opened for one specific peer. So an attacker would have to start by guessing source ip, target ip, and source port. Then the attacker would have to create a packet with a fake source ip, which could not get responses anyway. This packet is then discarded by the firewall, if the pc is on and only if it also contains a valid magic packet and the pc is off, it will turn on. The Wake on Lan protocol does not specify any response, so the attacker would not know, if anything happened. The worst case is that someone turns the pc on remotely without any indication to the attacker.
My use case is to access my powerful pc on the go from my notebook, without keeping it running all the time.
Thank you very much for this valuable information. My old DELL’s NIC listens on port 7 instead of 9 but your instruction worked perfectly.